Sammlung aller SSH/SSL relevanten und meist genutzten Dienste und deren optimale SSH/SSL Konfiguration.
Apache / Nginx
apache 2.4.18 | modern profile | OpenSSL 1.0.1e
Oldest compatible clients: Firefox 27, Chrome 30, IE 11 on Windows 7, Edge, Opera 17, Safari 9, Android 5.0, and Java 8
<VirtualHost *:443>
...
SSLEngine on
SSLCertificateFile /path/to/signed_certificate_followed_by_intermediate_certs
SSLCertificateKeyFile /path/to/private/key
# Uncomment the following directive when using client certificate authentication
#SSLCACertificateFile /path/to/ca_certs_for_client_authentication
# HSTS (mod_headers is required) (15768000 seconds = 6 months)
Header always set Strict-Transport-Security "max-age=15768000"
...
</VirtualHost>
# modern configuration, tweak to your needs
SSLProtocol all -SSLv3 -TLSv1 -TLSv1.1
SSLCipherSuite ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256
SSLHonorCipherOrder on
SSLCompression off
SSLSessionTickets off
# OCSP Stapling, only in httpd 2.3.3 and later
SSLUseStapling on
SSLStaplingResponderTimeout 5
SSLStaplingReturnResponderErrors off
SSLStaplingCache shmcb:/var/run/ocsp(128000)
nginx 1.10.1 | modern profile | OpenSSL 1.0.1e
Oldest compatible clients: Firefox 27, Chrome 30, IE 11 on Windows 7, Edge, Opera 17, Safari 9, Android 5.0, and Java 8
server {
listen 80 default_server;
listen [::]:80 default_server;
# Redirect all HTTP requests to HTTPS with a 301 Moved Permanently response.
return 301 https://$host$request_uri;
}
server {
listen 443 ssl http2;
listen [::]:443 ssl http2;
# certs sent to the client in SERVER HELLO are concatenated in ssl_certificate
ssl_certificate /path/to/signed_cert_plus_intermediates;
ssl_certificate_key /path/to/private_key;
ssl_session_timeout 1d;
ssl_session_cache shared:SSL:50m;
ssl_session_tickets off;
# modern configuration. tweak to your needs.
ssl_protocols TLSv1.2;
ssl_ciphers 'ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256';
ssl_prefer_server_ciphers on;
# HSTS (ngx_http_headers_module is required) (15768000 seconds = 6 months)
add_header Strict-Transport-Security max-age=15768000;
# OCSP Stapling ---
# fetch OCSP records from URL in ssl_certificate and cache them
ssl_stapling on;
ssl_stapling_verify on;
## verify chain of trust of OCSP response using Root CA and Intermediate certs
ssl_trusted_certificate /path/to/root_CA_cert_plus_intermediates;
resolver <IP DNS resolver>;
....
}
Quelle: https://mozilla.github.io/server-side-tls/ssl-config-generator/
SSL Webserver Test
Qualys hat eine tolle SSL Analyse Webseite, Link: https://www.ssllabs.com/ssltest/
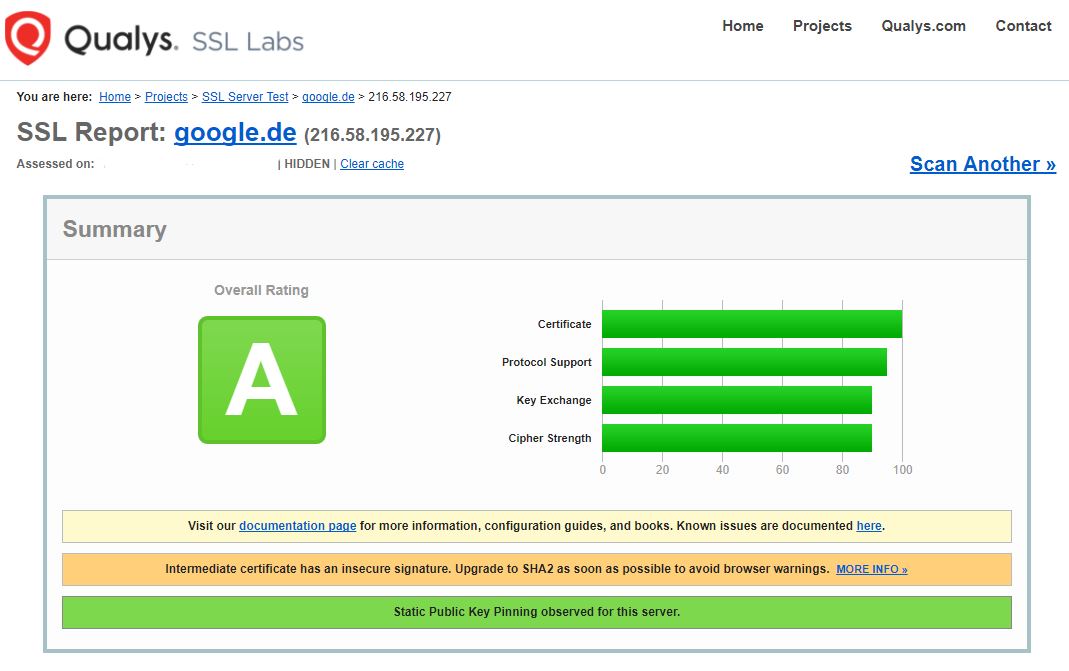
Beispiel google.de:
Es zeigt einen schnellen Überblick plus sehr detailierte Informationen was nicht passt oder was man verbessern kann.
Alternative check with nmap
max@cmkdevel:~$ nmap --script ssl-cert,ssl-enum-ciphers -p 443 www.google.de Starting Nmap 7.01 ( https://nmap.org ) at 2017-08-01 09:08 CEST Nmap scan report for www.google.de (172.217.17.35) Host is up (0.031s latency). Other addresses for www.google.de (not scanned): 2a00:1450:400e:804::2003 rDNS record for 172.217.17.35: ams16s29-in-f3.1e100.net PORT STATE SERVICE 443/tcp open https | ssl-cert: Subject: commonName=www.google.de/organizationName=Google Inc/stateOrProvinceName=California/countryName=US | Issuer: commonName=Google Internet Authority G2/organizationName=Google Inc/countryName=US | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha256WithRSAEncryption | Not valid before: 2017-07-19T11:48:30 | Not valid after: 2017-10-11T11:31:00 | MD5: f21e dd1d 579f 5ea3 1b3d 2e79 873d 616c |_SHA-1: f2af ac3f fb43 20be 9f6a b0fc 9356 808a f677 86fc | ssl-enum-ciphers: | TLSv1.0: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C | compressors: | NULL | cipher preference: server | TLSv1.1: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C | compressors: | NULL | cipher preference: server | TLSv1.2: | ciphers: | TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (secp256r1) - A | TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (secp256r1) - A | TLS_RSA_WITH_AES_128_GCM_SHA256 (rsa 2048) - A | TLS_RSA_WITH_AES_256_GCM_SHA384 (rsa 2048) - A | TLS_RSA_WITH_AES_128_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_AES_256_CBC_SHA (rsa 2048) - A | TLS_RSA_WITH_3DES_EDE_CBC_SHA (rsa 2048) - C | compressors: | NULL | cipher preference: server |_ least strength: C Nmap done: 1 IP address (1 host up) scanned in 3.31 seconds
Postfix
/etc/postfix/main.cf
smtpd_tls_mandatory_protocols = !SSLv2, !SSLv3 smtpd_tls_mandatory_ciphers=high tls_high_cipherlist=EDH+CAMELLIA:EDH+aRSA:EECDH+aRSA+AESGCM:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH:+CAMELLIA256:+AES256:+CAMELLIA128:+AES128:+SSLv3:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!DSS:!RC4:!SEED:!ECDSA:CAMELLIA256-SHA:AES256-SHA:CAMELLIA128-SHA:AES128-SHA smtpd_tls_exclude_ciphers = aNULL, eNULL, EXPORT, DES, RC4, MD5, PSK, aECDH, EDH-DSS-DES-CBC3-SHA, EDH-RSA-DES-CBC3-SHA, KRB5-DES, CBC3-SHA smtpd_tls_dh1024_param_file=/etc/ssl/dh2048.pem smtp_tls_mandatory_protocols = !SSLv2, !SSLv3 smtp_tls_protocols = !SSLv2, !SSLv3 lmtp_tls_mandatory_protocols = !SSLv2, !SSLv3 lmtp_tls_protocols = !SSLv2, !SSLv3 smtp_tls_security_level = may smtp_tls_loglevel = 1 smtpd_tls_auth_only = yes
Generate new Diffie Hellman Keys
openssl dhparam -out /etc/ssl/dh2048.pem 2048
Restart Postfix
service postfix restart
Mehr: http://www.postfix.org/TLS_README.html
Check Postfix SSL Configuration
Test mit openssl s_client
openssl s_client -starttls smtp -connect mailserver.example.org:25
Alternative mit nmap
nmap --script ssl-cert,ssl-enum-ciphers -p 993,995,25,587 -Pn mailserver.example.org
Dovecot
/etc/dovecot/conf.d/10-ssl.conf
ssl_cipher_list = EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA+RC4:EECDH:EDH+aRSA:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS:!RC4 #only for dovecot >=2.2.6, enforce the server cipher preference ssl_prefer_server_ciphers = yes #disable SSLv2 and SSLv3 ssl_protocols = !SSLv2 !SSLv3
Restart dovecot
service dovecot restart
Überprüfen mit openssl s_connect
openssl s_client -connect mailserver.example.org:993 openssl s_client -connect mailserver.example.org:995
Alternative mit nmap
nmap --script ssl-cert,ssl-enum-ciphers -p 993,995 -Pn mailserver.example.org
SSH
/etc/ssh/sshd_config
# Remove dsa hostkeys HostKey /etc/ssh/ssh_host_ed25519_key HostKey /etc/ssh/ssh_host_rsa_key HostKey /etc/ssh/ssh_host_ecdsa_key KexAlgorithms curve25519-sha256@libssh.org,ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group-exchange-sha256 Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes256-ctr Macs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512,hmac-sha2-256 AuthenticationMethods publickey LogLevel VERBOSE Subsystem sftp /usr/lib/ssh/sftp-server -f AUTHPRIV -l INFO PermitRootLogin No UsePrivilegeSeparation sandbox
Achtung ! DSA SSH Keys werden danach nicht mehr funktionieren.
Restart SSH
service ssh restart
OpenVPN
/etc/openvpn/openvpn.conf
tls-version-min 1.2 tls-cipher TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384 cipher AES-256-CBC auth SHA512 reneg-sec 60
Quelle: https://community.openvpn.net/openvpn/wiki/Hardening / https://gist.github.com/pwnsdx/8fc14ee1e9f561a0a5b8